User experience
Plaid user experience guide
Plaid Link is the UI component users interact with to link their accounts to an app using Plaid. Your institution will show up in Plaid Link after you go live on Core Exchange.
Institution selection
A user wants to connect their financial account to an app called WonderWallet. WonderWallet sends them to Plaid Link where they can select their financial institution. In this example, the financial institution is called First Platypus Bank.
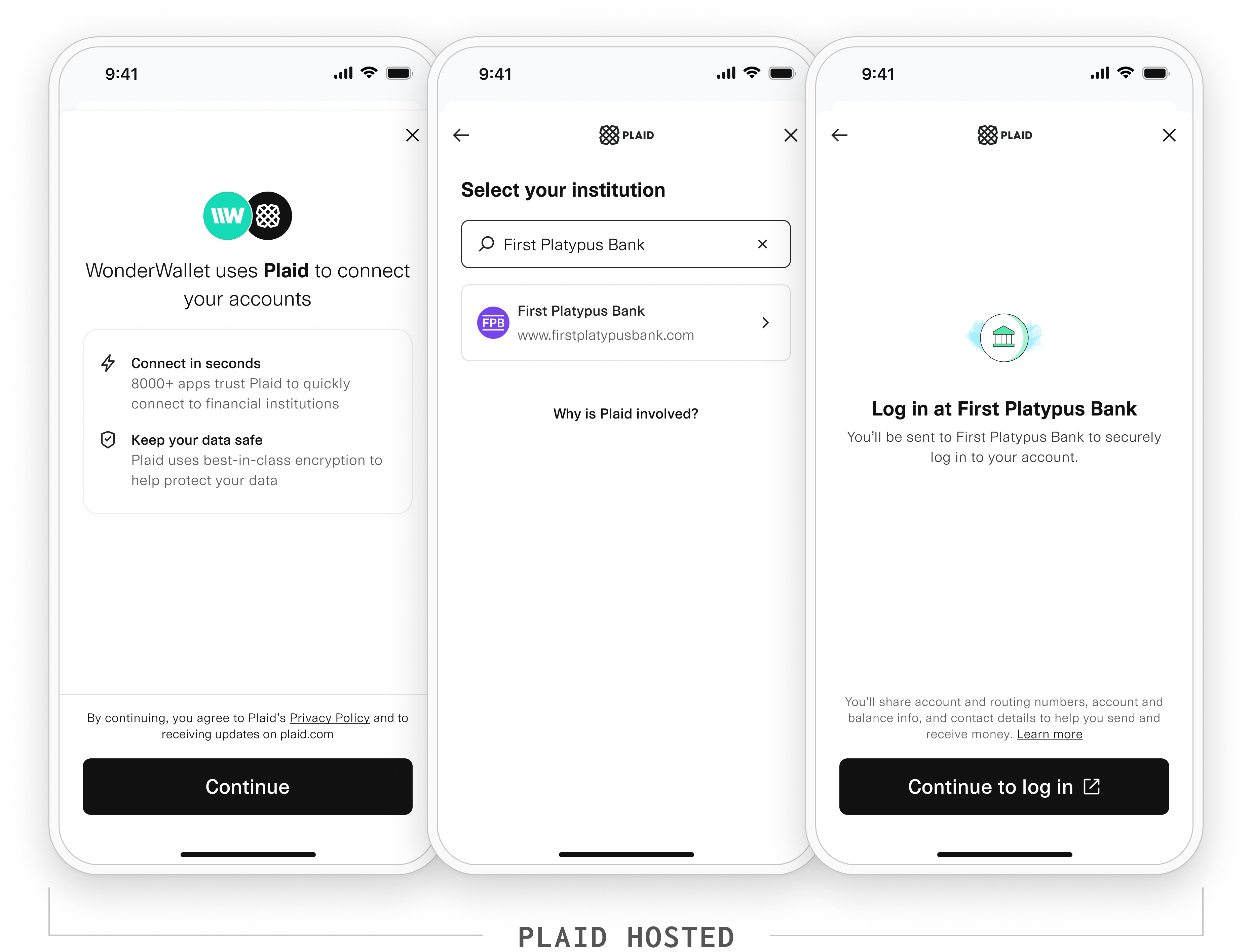
Data transparency messaging
Data Transparency Messaging (DTM) gives consumers a way of understanding the data types needed to power an app or service that they want to use.
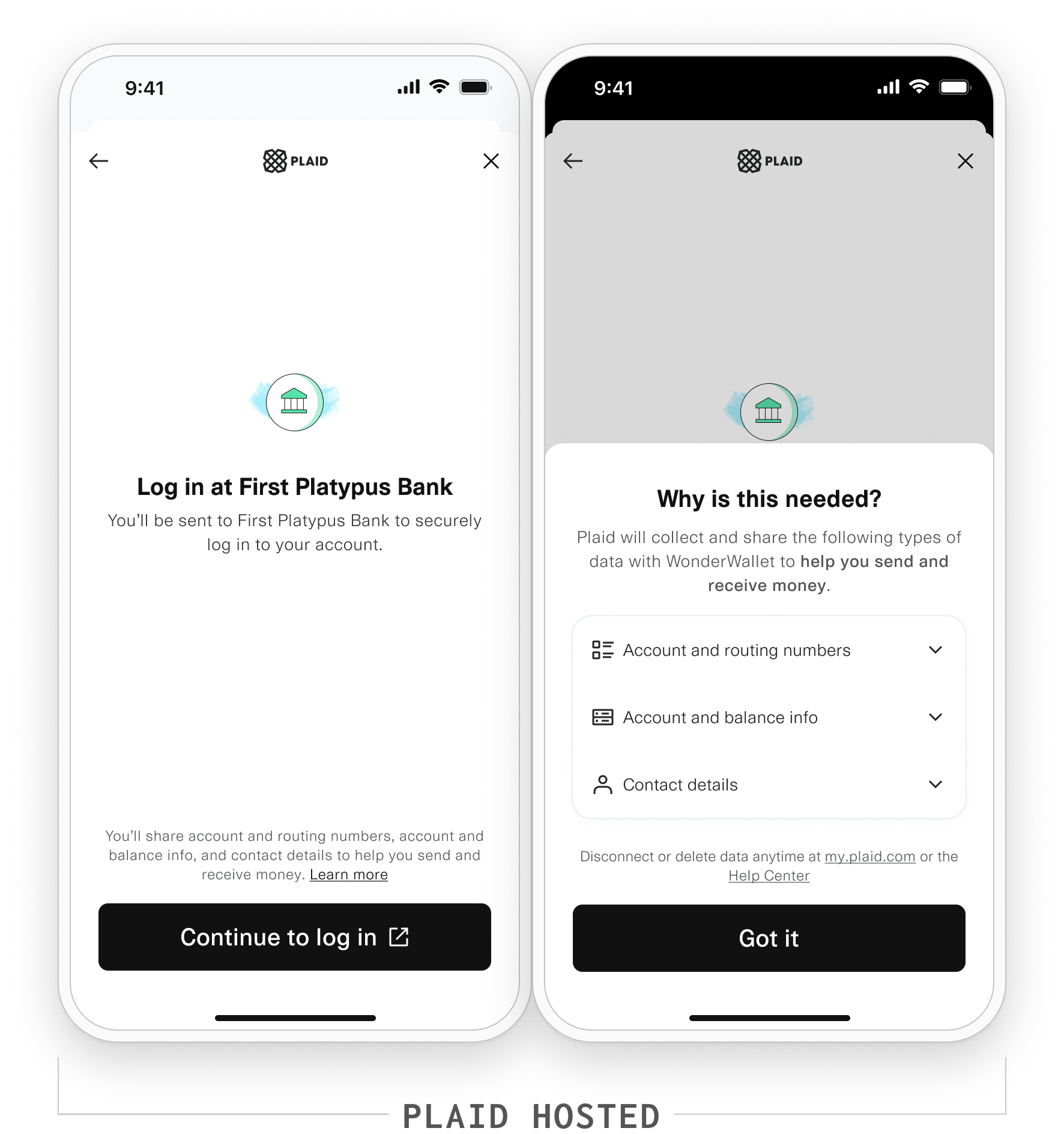
This enables Plaid and our customers to meet 1033 requirements: the 1033 rule requires that Plaid and our customers (third parties) disclose the data types they are requesting access to, and for which use cases. Additionally, Plaid customers need to ensure customer authorization is captured. With DTM, Plaid shows data types and use cases on behalf of the customer in Link, and then captures the authorization.
DTM will appear as a footer on the Pre-OAuth pane for all users that connect through OAuth.
Plaid and Plaid customers will only access the specific data the user has consented to via DTM. If additional data is required, the consumer will need to provide additional consent.
When an item has been created with DTM, Plaid will also expose the consent records including the use case, data types, and time stamp of consent via Permissions Manager—this ensures you have full visibility into the consumers’ consent, enabling you (as a Data Provider) to “confirm” authorization under the rule. If consent status or scope change on an item, such as if a user revokes access or grants additional access, these changes will also be reflected in the Permissions Manager records.
To ensure a consistent user experience and to avoid repetition, Plaid recommends that you do not include a description of the data scopes/fields shared in your OAuth flow.
Authentication Guidance
OAuth
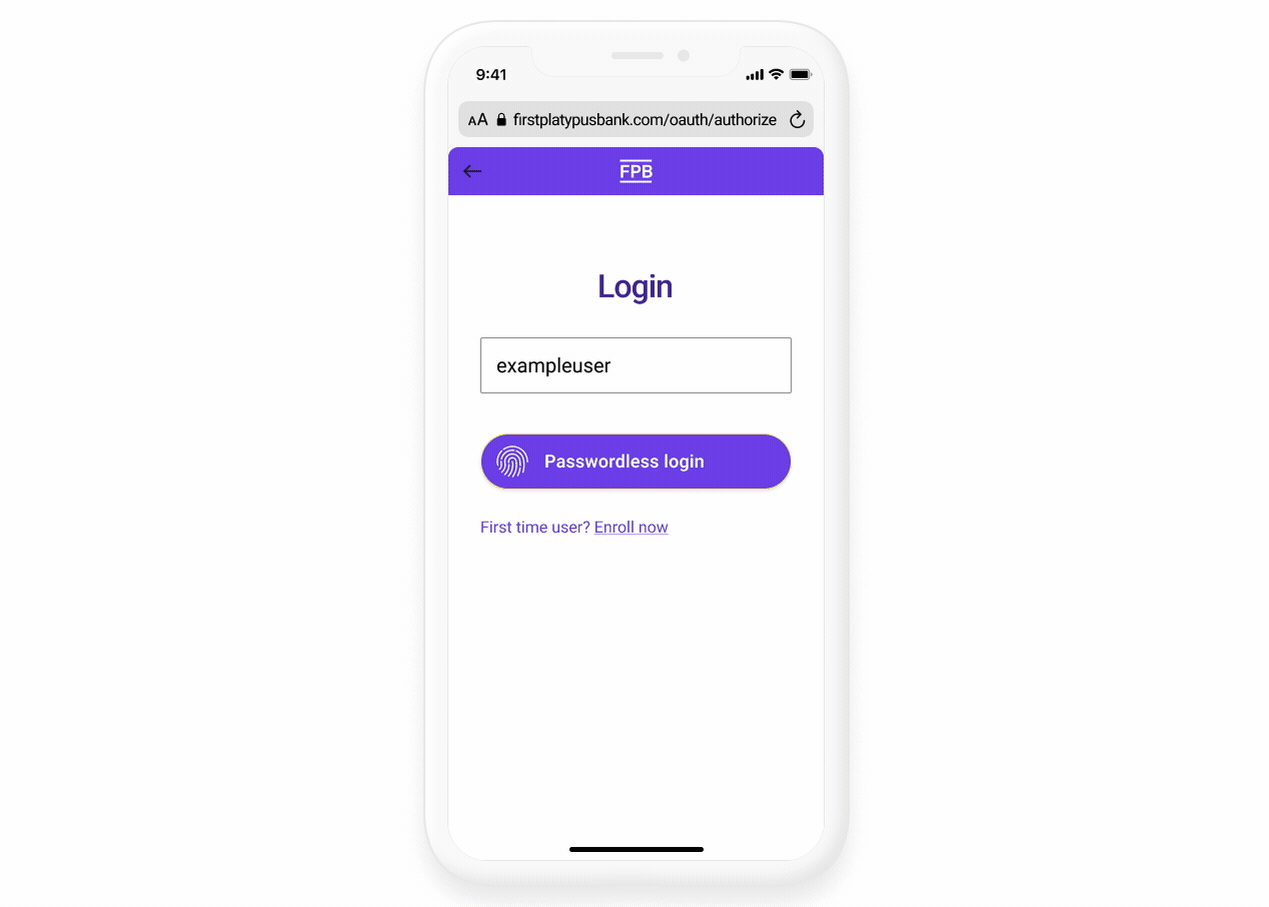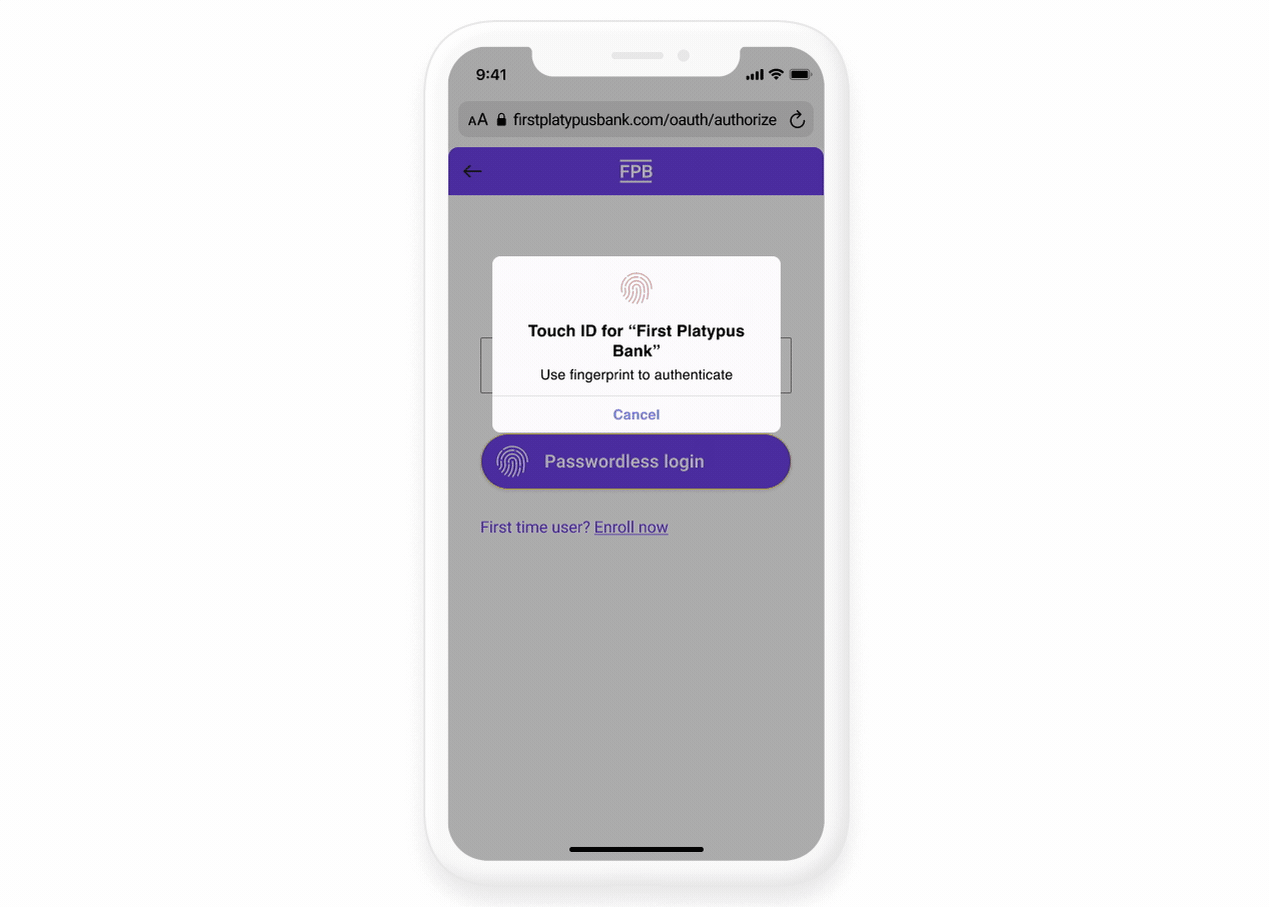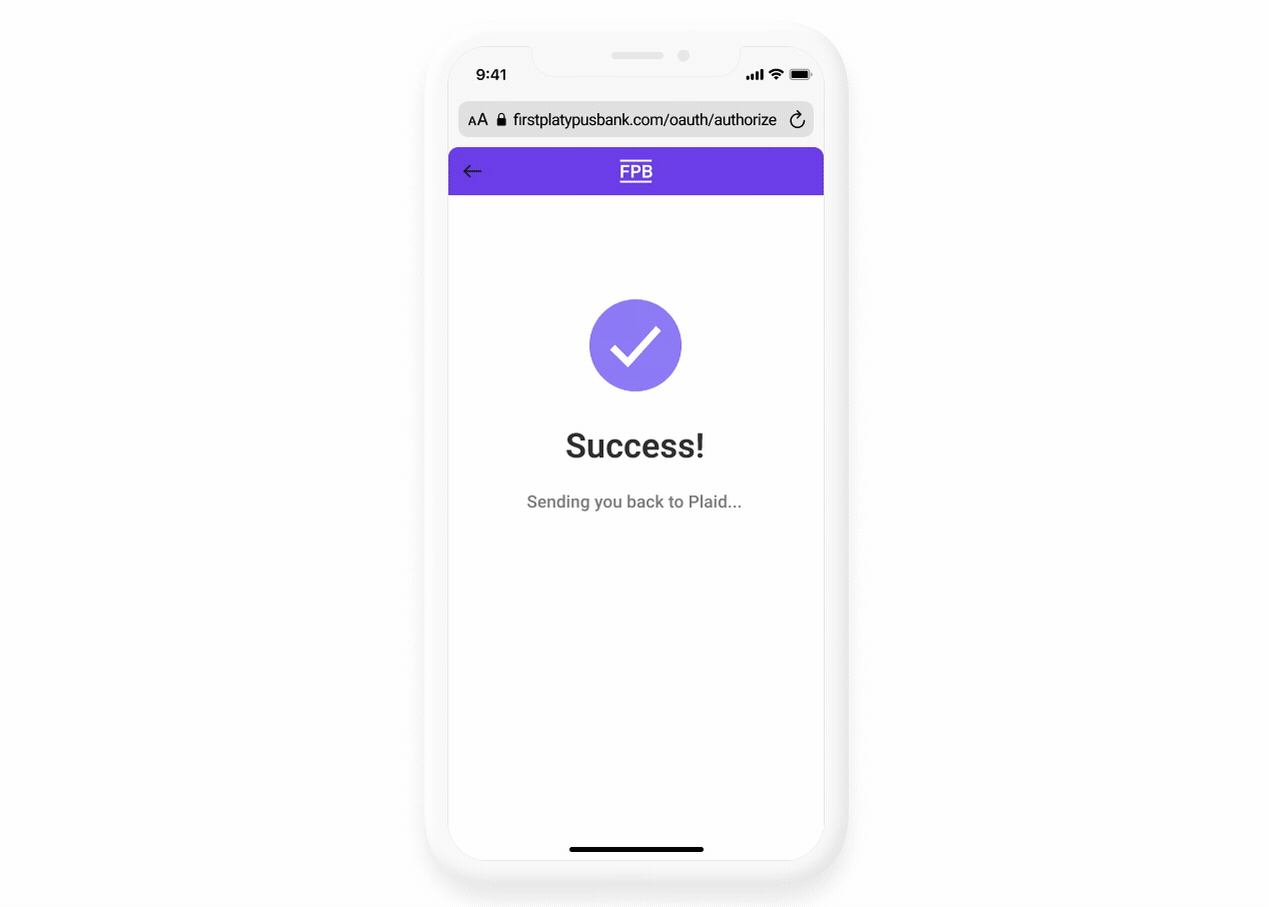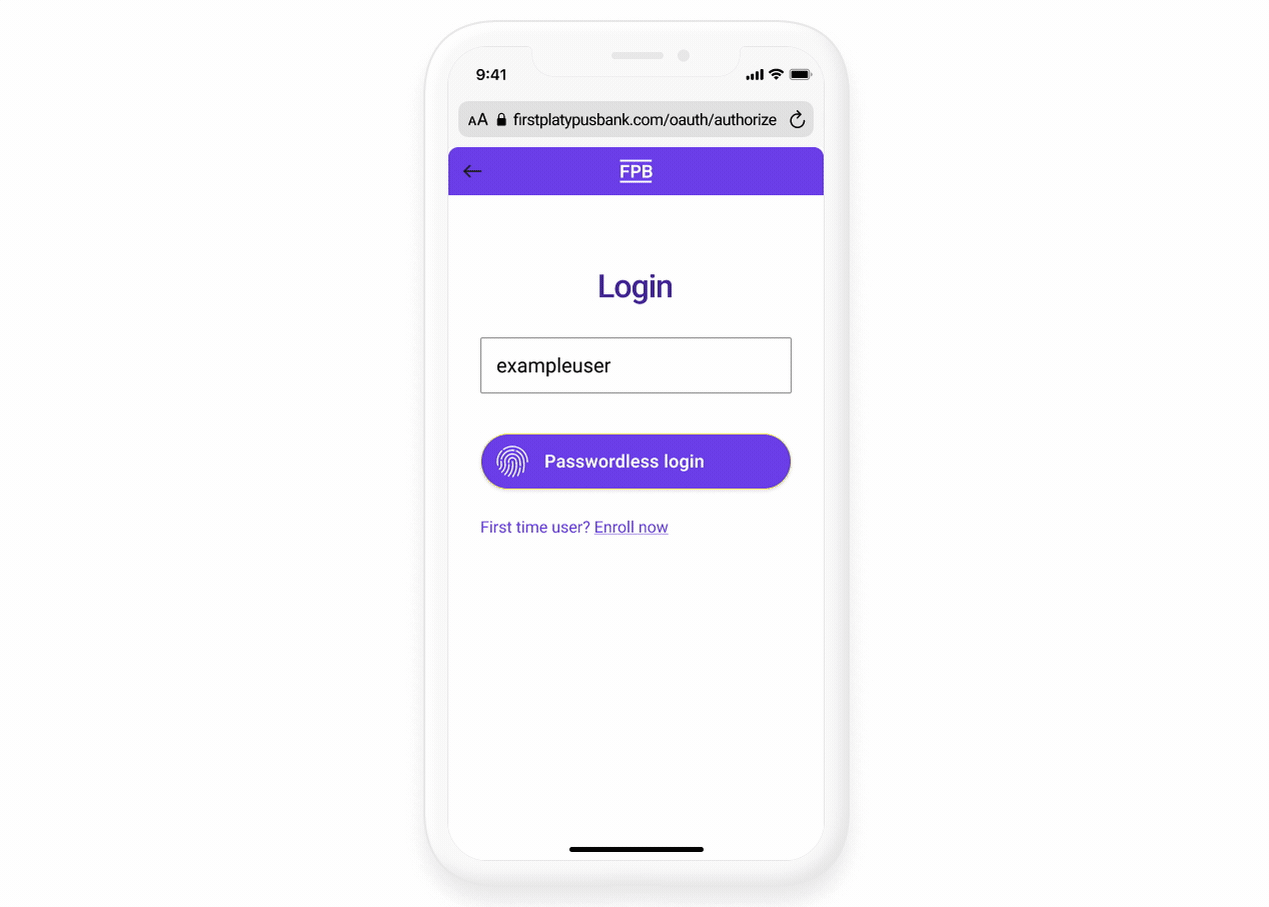
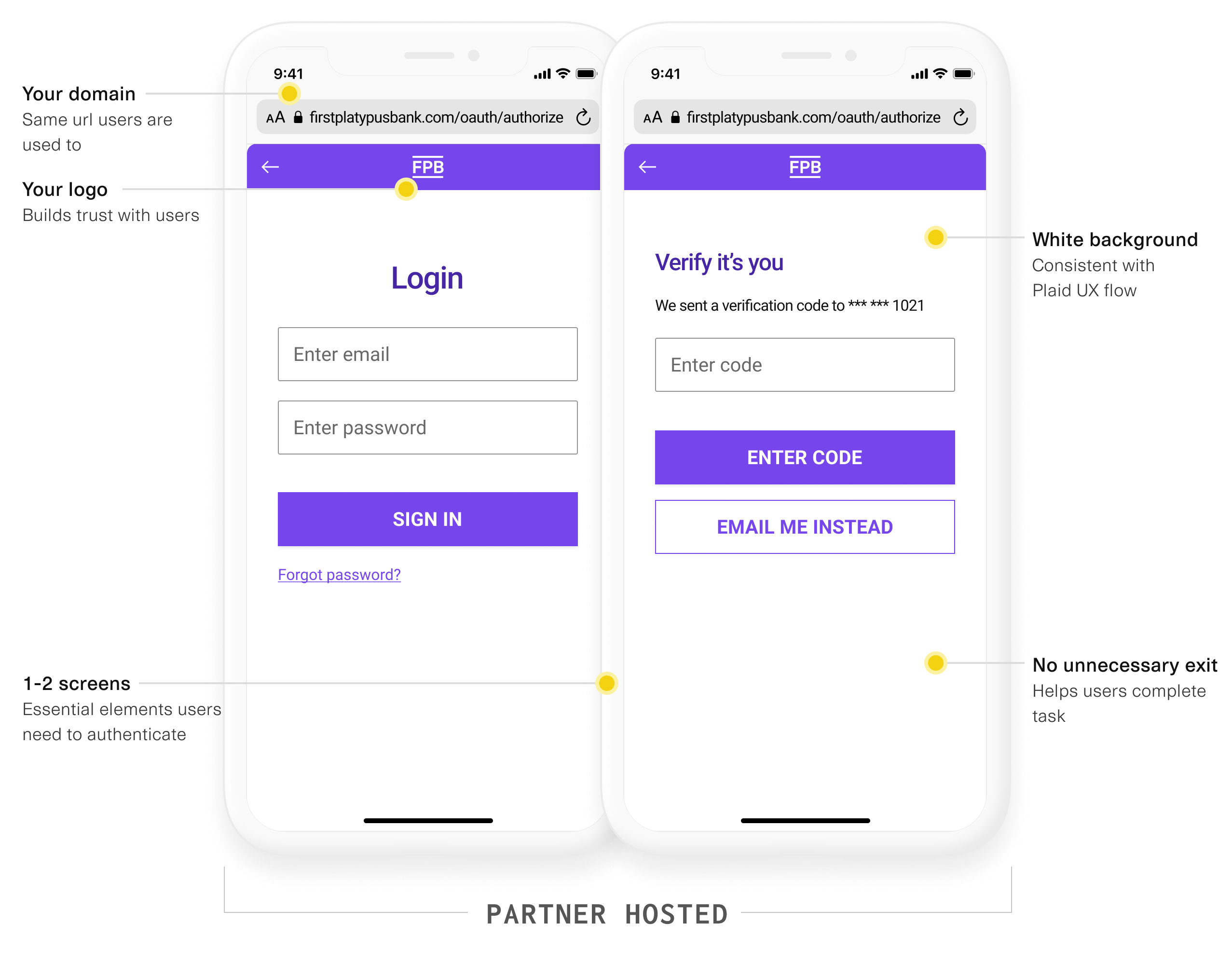
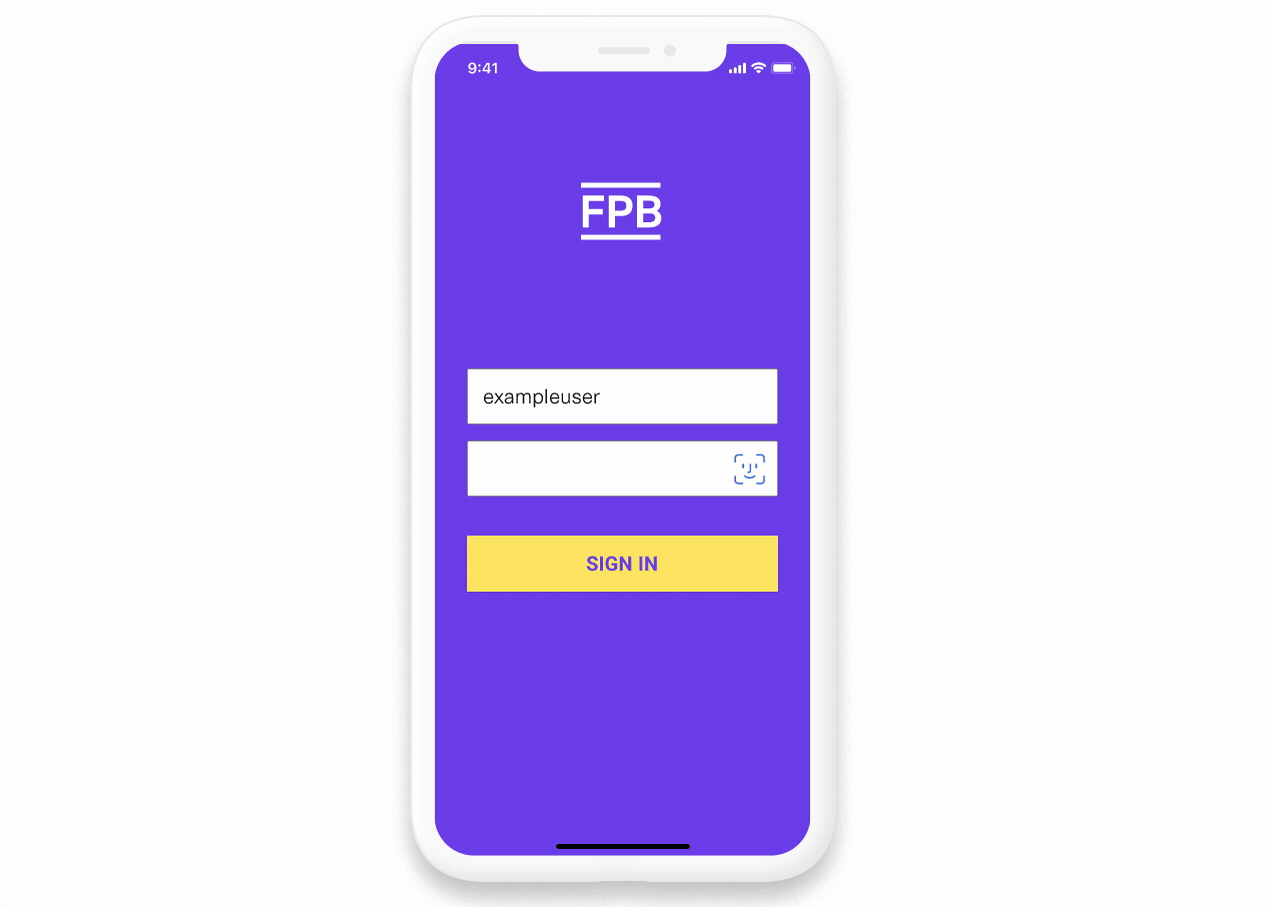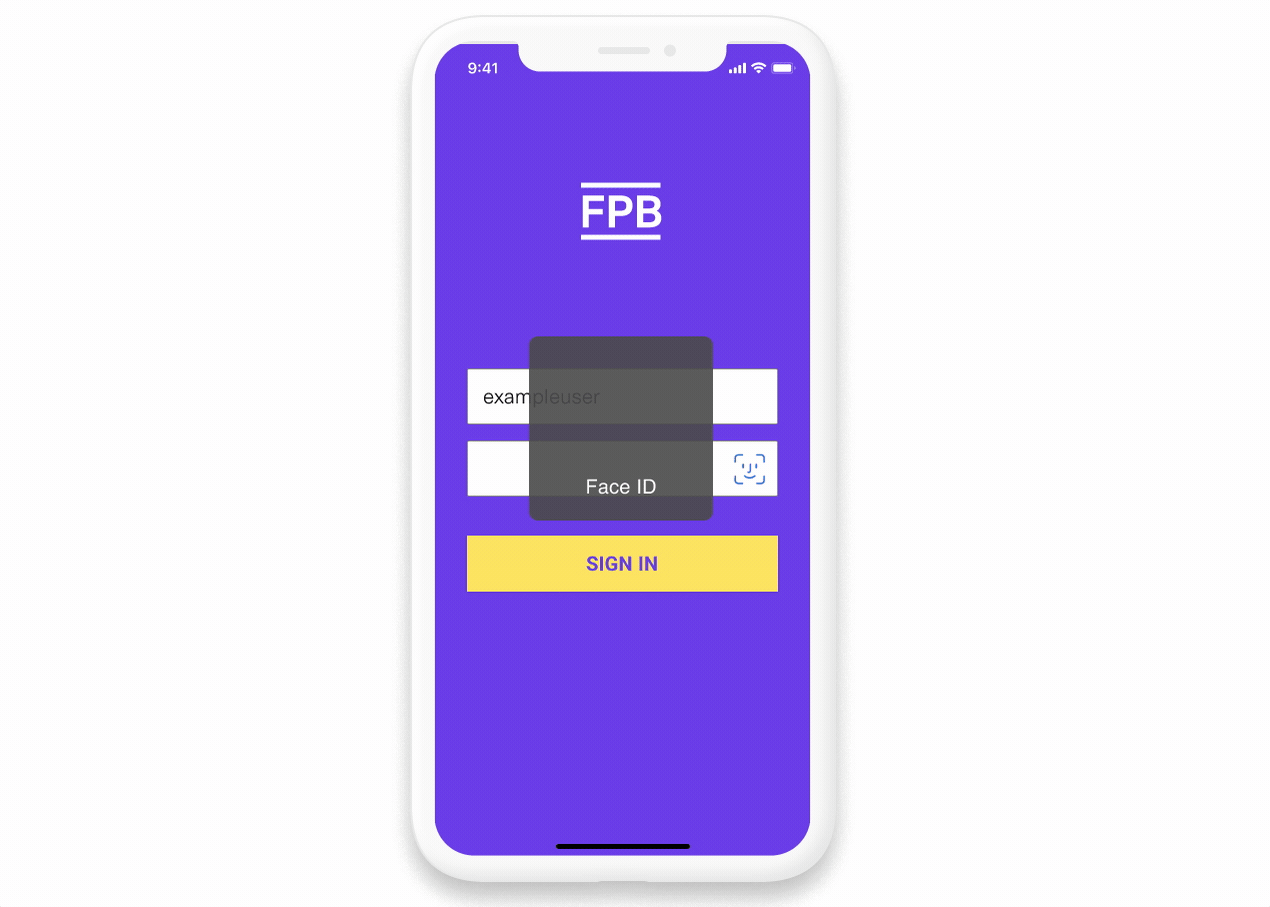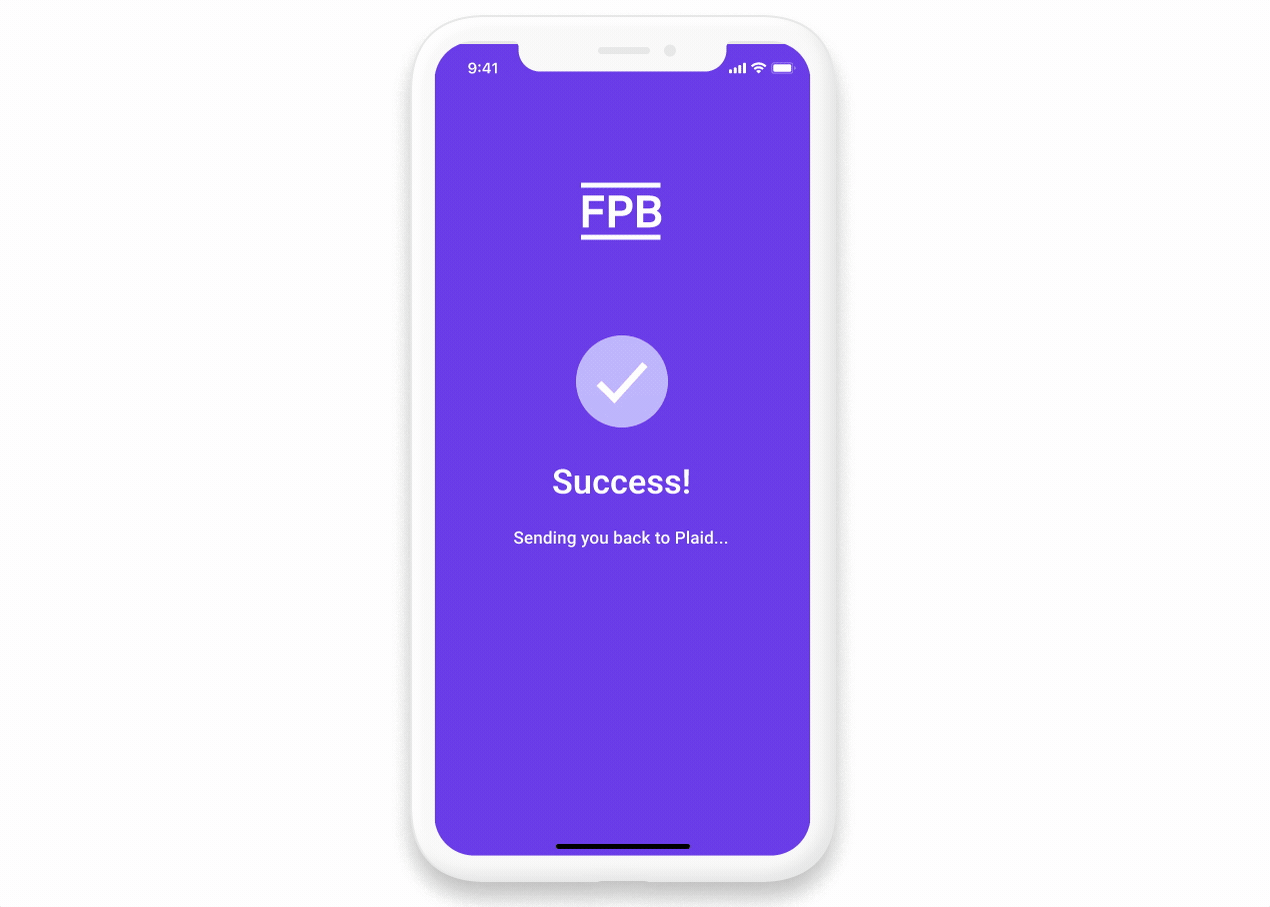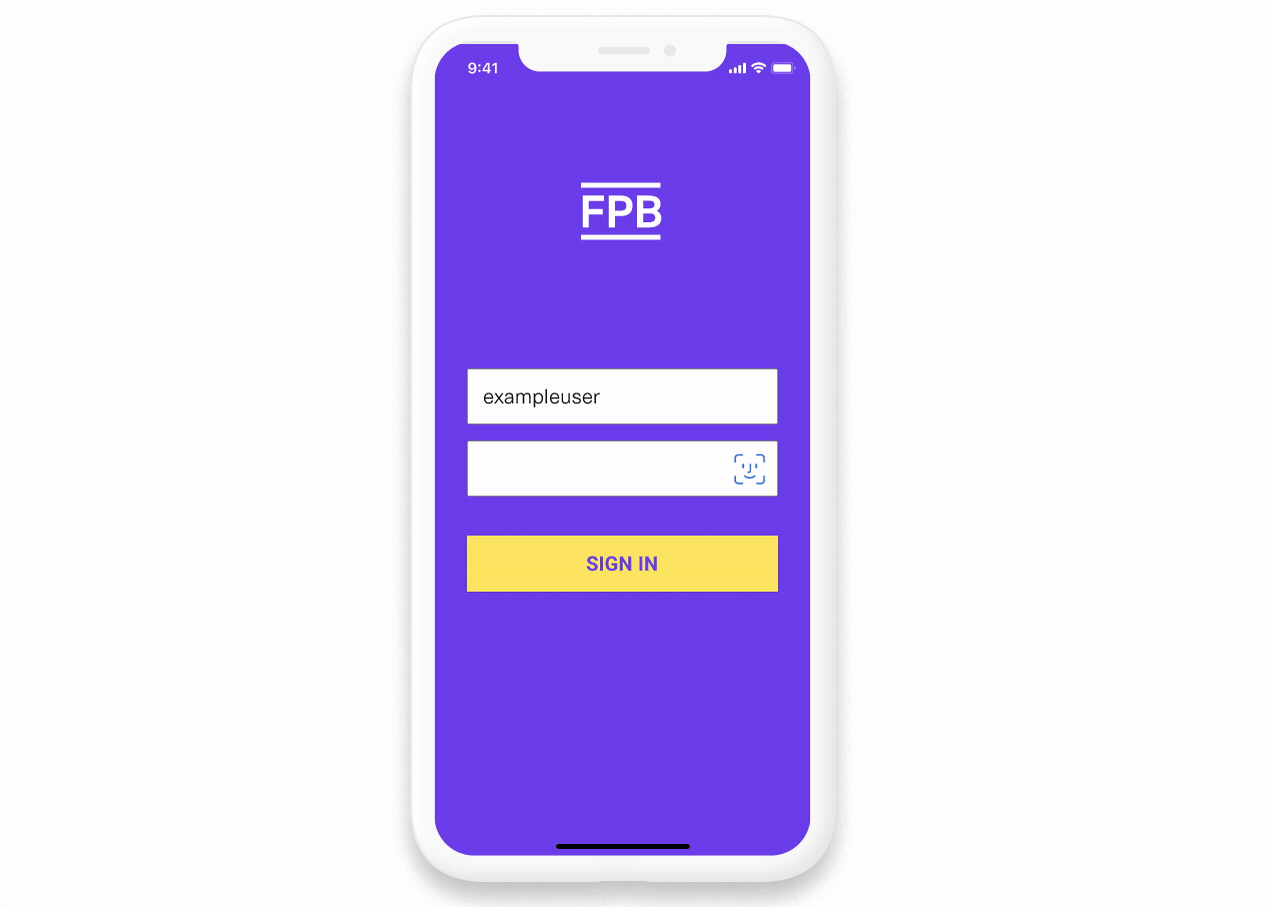
The user is asked to authenticate with First Platypus. Plaid recommends you do this using the OAuth 2.0 protocol.
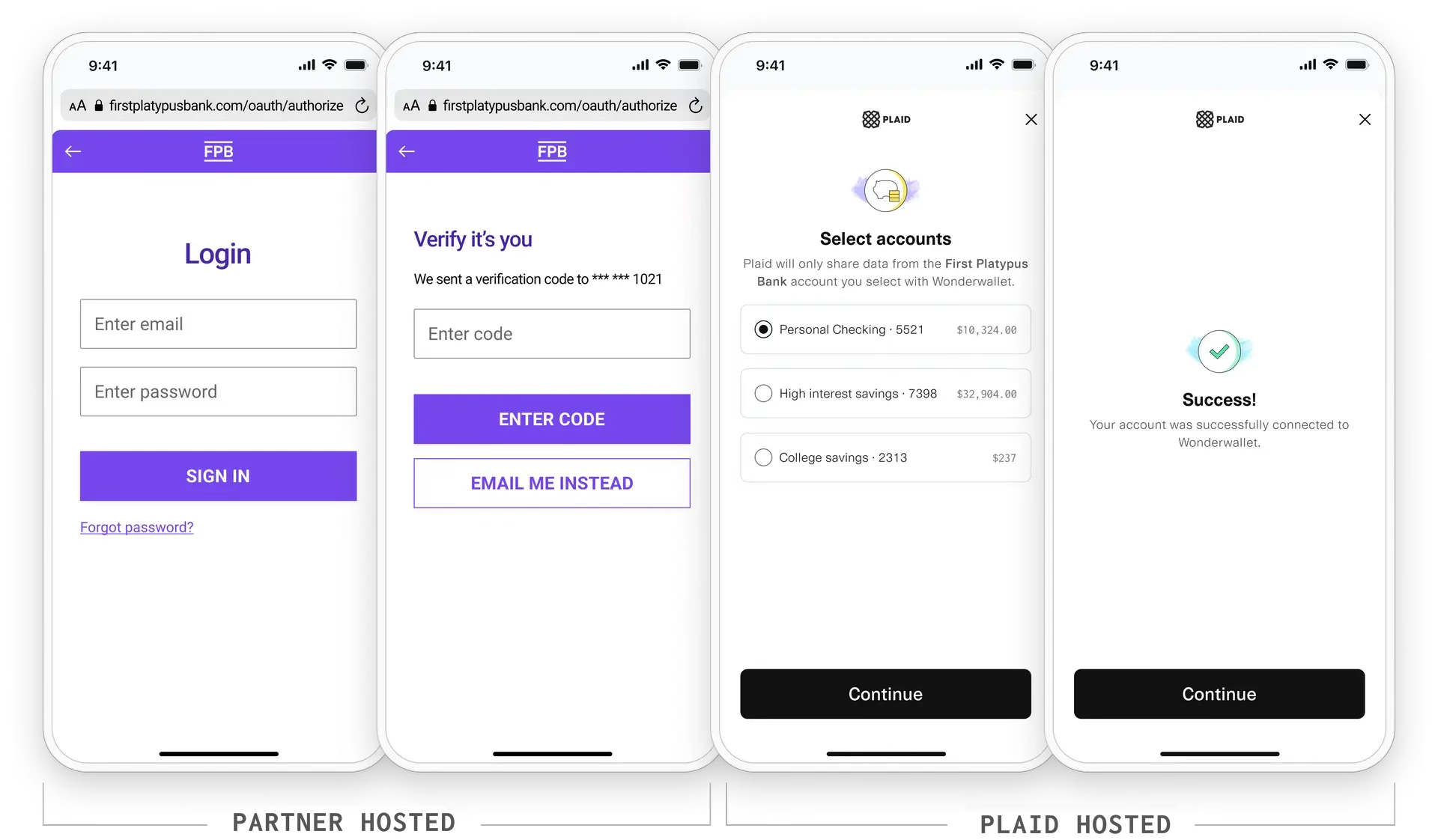
You own the OAuth user experience and host it on your domain. We encourage you have two screens with your logo prominently featured: a login screen and two-step verification screen.
Your OAuth flow must implement strong authentication and not solely rely on username/password, incorporating multi-factor authentication with one-time passcodes or stronger methods like push-based authentication or biometrics through App2App or WebAuthn.
Account selection
If the user has more than one financial account, the user returns to Plaid Link and is asked to select which accounts they’d like to link. The user then sees a success screen. Tapping the continue button will return them to WonderWallet.
Returning user experience
Plaid’s returning user experience streamlines onboarding for users who have previously connected a financial account with Plaid via your institution’s OAuth and API integration.
In Link, a user can choose to be remembered by Plaid by entering their phone number and then verifying it using a one-time password. Next, the user connects their account through your OAuth flow, which would be associated with their phone number. When the same user wants to connect their account to another app, Plaid enables the user to do so using their phone number and secure authentication methods like one-time passcodes and passkeys. This streamlined experience has built-in security controls and advanced monitoring that automatically detect suspicious activity and help prevent fraud.
As a data partner for Core Exchange, you’re automatically enabled for this streamlined experience with no integration work required. Your users can now opt-in and benefit from a faster way to securely connect their accounts to apps and services on the Plaid network.
Optional components
App2app
App2app is a mechanism that allows mobile apps performing OAuth2 or OpenID Connect based authentication to offer a much simpler faster flow if the user already has an app provided by the authorization server owner installed on their mobile device. The example below uses App2app.
The user is brought to the First Platypus app to authenticate where they can use biometrics.
WebAuthn
We also recommend using WebAuthn for web-based authentication. Users can enroll and then easily use biometrics to authenticate on any web browser.